This page covers the core principles, policies, and measures deployed to ensure the resilience and security of the service. Where appropriate this document may refer to other more detailed resources that are available via our Support Portal or by request.
Contents
Introduction
Matrix Booking is an award-winning resource management Software as a Service (SaaS) system. We provide services to both the public and private sectors in 12 countries, and we’re proud of our performance and security record.
This page is designed for customers, hub operators, and tenants that are using or evaluating the Matrix Booking suite within their organisation.
Note: this page contains security information about the Matrix Booking system, and therefore, it should only be utilised within the organisation authorised. Distribution within the organisation should be limited to essential personnel only.
Technology overview
The Matrix Booking service is built on an open and secure enterprise architecture through Amazon Web Services (AWS), which can be accessed via a common API by a suite of apps.
Matrix Booking technical architecture
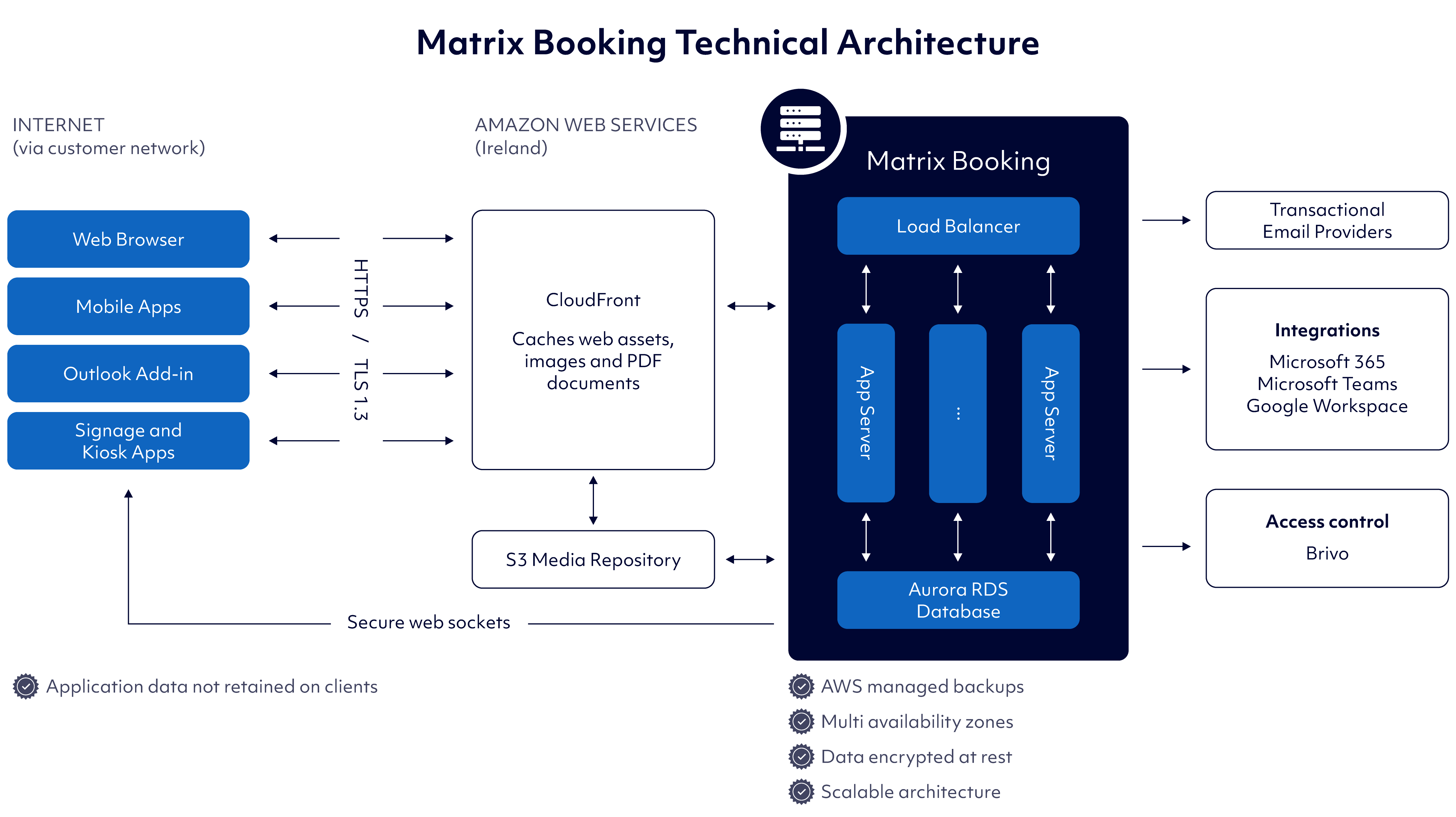
Data flows
The diagram below outlines the typical data flows within the various components of the platform:
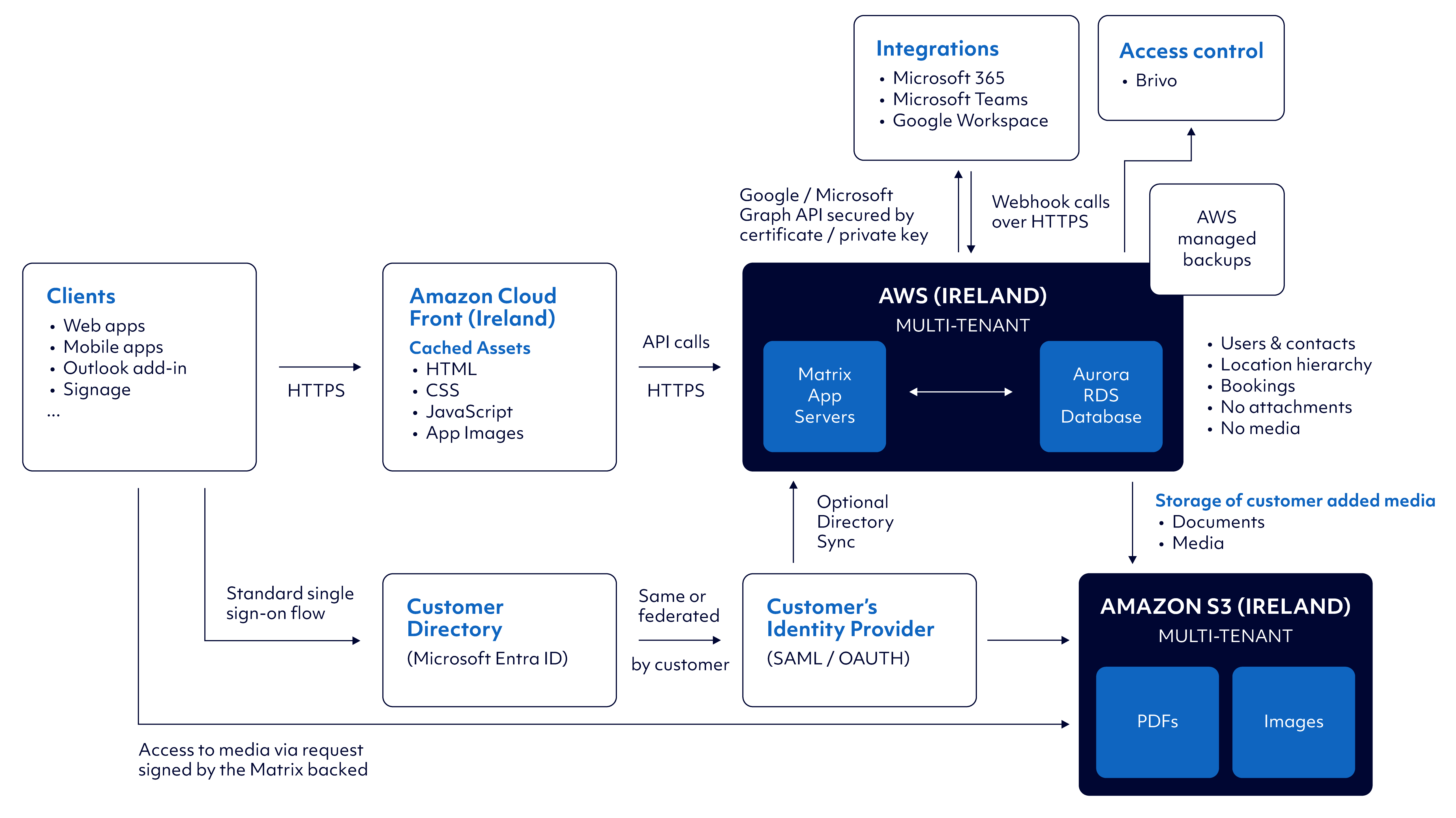
Functional design
Presentation and client interfaces
Matrix Booking provides several interfaces that all communicate securely over HTTPS / TLS 1.3 to the back-end servers.
These include:
-
web app
-
native iOS and Android apps
-
Cordova apps running on Android (for example, Signage and kiosk apps)
-
Outlook add-in
-
Brivo Access Control
Middleware
Matrix Booking uses Amazon CloudFront to cache web assets, images, and PDF documents to ensure they are available from a location close to the user to reduce latency.
Back-end
The Matrix Booking platform is hosted on AWS in Ireland (eu-west-1 region), which uses:
-
load balanced application servers
-
scalable using Elastic Kubernetes Service, with clusters across multiple Availability Zones
-
multiple scalable Availability Zones via Amazon Aurora RDS database
-
supplementary location information (for example, images or floor plans) are hosted on Amazon S3
-
all data is encrypted in transit and at rest
-
AWS: dynamoDB, SQS – Message Queueing Service, KMS – Key Management Service, and Lambda services
Physical storage
All personal and booking data is stored in the Amazon Aurora RDS database.
Additional services
Matrix Booking uses several transactional email providers to send notification, alert, and calendar emails to users:
-
MailGun (for those requiring an entirely EU-hosted solution only, this should be specified during your onboarding)
-
Mandrill by MailChimp (not used for EU-only hosted customers)
-
SendGrid (not used for EU-only hosted customers)
-
AWS SES Simple Email Service
Technical requirements
This section outlines the requirements for the different components of Matrix Booking.
Matrix Booking web app
The web app simply needs an up-to-date browser with no requirement for any plug-ins. The list of supported browsers is:
-
Chrome
-
Firefox
-
Safari
-
Edge
Warning: support for Internet Explorer 11 is no longer available. Use 1 of the browsers in the above list.
Matrix Booking mobile applications
Native iOS and Android mobile apps are available from both the Apple App Store and Google Play. The Matrix Booking suite currently supports the following minimum mobile device operating system versions:
-
iOS 15.6 or above
-
Android 9 or above
Matrix Booking can offer a full Hardware-as-a-Service (HaaS) subscription for devices that can include device selection, procurement, configuration and setup, and installation as well as remote monitoring and support.
Firewall and IP addresses
Matrix Booking requires access to several known domains to serve both its data and related resources (for example, images or documents). These will need to be permitted on any firewalls or proxies in the organisation.
Note: where the Outlook add-in is used, some firewalls will treat traffic from it in a different way than calls originating from a browser and may need additional configuration.
Accessibility
The Matrix Booking digital team is committed to making our online services accessible to all users in accordance with level AA of the Web Content Accessibility Guidelines (WCAG 2.2).
Accessibility limitations
Our products include third-party technologies and features that cause accessibility issues. These include:
-
Adobe PDF documents
-
Google Maps
We are making every effort to overcome these limitations and aim to provide accessible alternatives where improvements cannot be made.
Assistive technologies
We test our products using a variety of screen readers and browsers. The latest versions of the following assistive technologies provide the most accessible experience.
-
JAWS screen reader
-
NVDA screen reader
-
VoiceOver screen reader
Note: you may experience issues with older versions of these technologies.
Further details
Integrations
Single sign-on and Active Directory integration
The diagram below outlines the Matrix Booking directory integration processes and technical stack. Multiple directories can be connected to a single instance and 1 instance can also have multiple access methods depending on the user type (for example, single sign-on (SSO) for staff or username and password for third-party supplies):
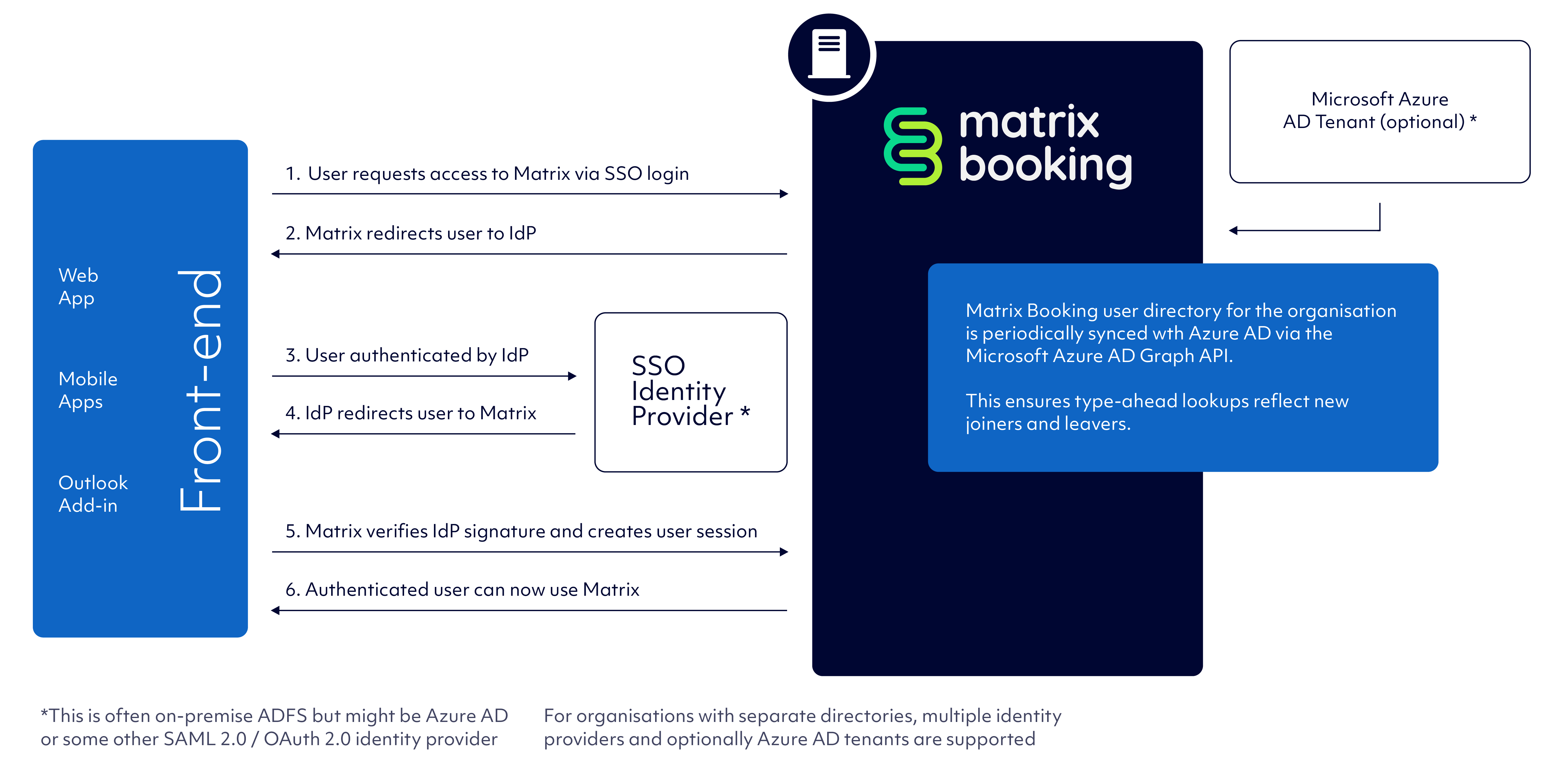
Single sign-on
Matrix Booking supports SSO using the following:
-
any SSO provider using SAML 2.0. For example:
-
Microsoft Entra ID (formerly Azure Active Directory)
-
Google Workspace
-
Okta
-
-
OAuth 2.0 with Microsoft Entra ID
Depending on the chosen means of SSO, customers will provide security metadata and add Matrix Booking as an approved app:
-
for SAML 2.0, this will include:
-
providing URL to the identity provider metadata
-
configuring Matrix Booking as a service provider
-
configuring SAML response to include required fields
-
-
for OAuth with Microsoft Entra ID, this will include:
-
registering Matrix Booking as a relying party
-
providing Matrix Booking with configured client ID and secret key
-
Microsoft Entra ID directory synchronisation
Matrix Booking can be configured to permit users to be created or deactivated through synchronisation with Entra ID. To facilitate this the following is required:
-
Matrix Booking registered as an app
-
granted permission to several Active Directory and Graph API functions
-
create a secret key
-
provide Matrix Booking with the following information:
-
application ID
-
Graph API endpoint
-
secret key
-
Microsoft 365
Matrix Booking permits direct integration with Microsoft 365 to ensure that bookings made in Matrix Booking are replicated directly into Microsoft 365 and bookings made in Microsoft 365 are processed by Matrix Booking. This integration requires the creation of an App Registration in Entra ID with appropriate access to several Graph API endpoints as outlined in the Matrix Booking Microsoft 365 integrations setup guide. These are:
-
Calendars.ReadWrite
-
Directory.ReadAll
Note: access will be protected using an X.509 certificate, which will be provided by Matrix Booking.
Outlook add-in
Matrix Booking provides an Outlook add-in compatible with Outlook 2010, 2013, and 2016 for Windows. This add-in is delivered in 1 of the 2 installer files (as .msi files):
-
Standard Installer – enabled by default:
-
installs the add-in so that it’s available for all users of the Windows desktop on the given machine
-
-
Extended Installer – disabled by default:
-
installs the add-in so that it’s disabled for all users by default, until a custom registry key is applied for each user. Whilst this installer can be used with local Windows PC setups, it’s intended for use with virtual desktop environments when the add-in should be installed for all users, but only made available to subsets of the virtual desktop user base
-
Several pre-requisites are required for the add-in:
-
Microsoft .NET Framework 4.8 or above
-
Microsoft Visual Studio Tools for Office Runtime
Microsoft Teams
Matrix Booking permits Microsoft Teams meetings to be created from within Matrix Booking and have these attached to the booking and invitations. This requires the creation of an App Registration in Entra ID (the one used for Microsoft 365 integration can be reused if preferred). Once created, a user with admin credentials can provide the appropriate details in Matrix Booking and grant the permissions required.
Note: all details are outlined in the Microsoft Teams integration guide.
Brivo Access Control
Matrix Booking can be configured to work with your Brivo Access Control system and manage physical access of users to a location. Users in your Brivo instance need to be synchronised with your Matrix Booking account, which can be done via Active Directory. These users can be configured to restrict access to days that they have bookings for. To facilitate this, you need to:
-
have Matrix Booking registered as an app in your Brivo instance
-
have a Matrix Booking user created in your Brivo instance for API access
-
provide your Account Manager with the following information:
-
client ID
-
client secret
-
Brivo API username and password
-
API key
-
Note: to discuss adding Access Control, contact your Account Manager.
Availability, capacity, and performance monitoring
Availability monitoring and management
The Matrix Booking SaaS platform is subject to continuous availability and performance monitoring, supported by proactive system health checks to minimise user-impacting incidents.
Monitoring includes real-time endpoint monitoring and alerting that continuously assess key user journeys and service availability.
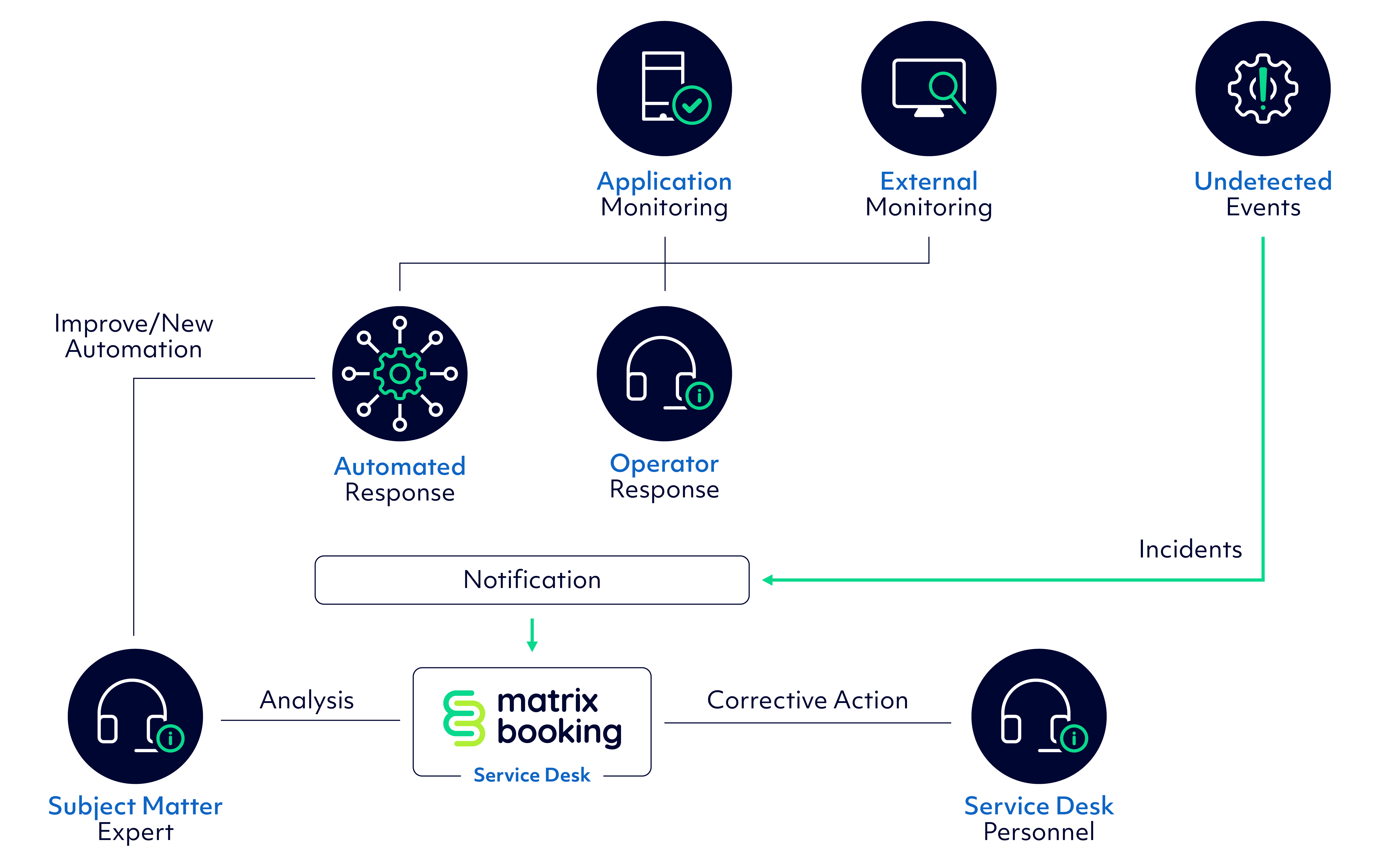
Monitoring, logging, and incident management tooling are deployed on infrastructure that is logically separate from the core Matrix Booking production environment, ensuring resilience and independence of controls.
Availability monitoring is supported by:
-
Real-time application and infrastructure metrics for cloud-based services.
-
Centralised application logging with alerting and analytics.
-
Real-time endpoint monitoring and alerting of key services and APIs.
-
Alerts integrated with Level 1 support for incident triage, escalation, and resolution in line with defined incident management procedures.
Service availability, incidents, and planned maintenance are communicated via the Matrix Booking Status Page, providing customers with current and historical service status information.
Capacity management
Matrix Booking is a SaaS platform that allows customers to add resources, users, and modules as and when they require. There’s no requirement for Matrix Booking customers to install any software or infrastructure. All that’s needed is an internet connection.
The Matrix Booking platform is based on a scalable web platform (AWS with Kubernetes) to respond to demand. Scalability is provided by:
-
load balanced service tiers that can be scaled out horizontally in response to demand
-
a data tier based on the Amazon Aurora RDS database system
-
load balanced network connections
-
performance and capacity management across the development cycle and carrying through to support, which includes continuous monitoring and performance testing
Performance management
We take several steps to ensure the performance of the Matrix Booking solution:
-
regular performance monitoring and capacity management
-
prerelease performance tests
-
an API-centric approach with light weight JSON data transferred between client devices and the Matrix Booking engine to minimise network bandwidth requirements
-
use of a content delivery network to cache assets closer to our customers
Several monitoring tools provide real-time analysis of performance and load and can proactively alert when non-standard metrics are identified. These include:
-
detailed app logs and metrics sent in real-time to DataDog, a log management and monitoring service for cloud-based apps
-
Pingdom, a global performance and monitoring service for websites and web apps
Monitoring alerts are routed to our Operations and Support Teams. Investigation by our combined Development and Operations teams follows according to the severity of the incident. If required, the Support Team manage communications with customers.
Business continuity and disaster recovery
Data backup and recovery
Data is stored by our hosting provider AWS using Amazon Aurora. An Aurora DB cluster is fault tolerant by design. The cluster volume spans multiple Availability Zones in a single AWS Region (eu-west-1 Ireland) and each Availability Zone contains a copy of the cluster volume data. This functionality means that the DB cluster can tolerate a failure of an Availability Zone without any loss of data and only a brief interruption of service.
Aurora backs up the cluster volume automatically and retains restore data for the length of the backup retention period, which is 35 days. Aurora backups are continuous and incremental so you can quickly restore to any point within the backup retention period. No performance impact or interruption of database service occurs as backup data is being written. Aurora backups are stored in Amazon S3.
Matrix Booking ensures the integrity of the backups by performing periodic full restores to a separate secure environment.
Business continuity planning
Matrix Booking has a full business continuity and pandemic response plan. The key principles behind our planning is that we’re resilient to the loss of physical locations and can function robustly as a remote team:
-
Our services and tools aren’t dependent on any physical location.
-
Our services and tools are deployed to resilient cloud infrastructure.
-
Working in distributed teams, in different locations (including home working) is a standard part of our working practices.
-
Security of Matrix Booking, customer services, and data will be maintained in a continuity scenario.
The key stages are outlined below:
-
When criteria outlined for invoking the business continuity plan (BCP) have been met:
-
Decide on Business Continuity Manager (BCM) and other recovery team members.
-
Set up recovery team chat channel.
-
-
Notify staff of disaster via Matrix Booking All email – initial step is for home working until further notice.
-
Home working procedures:
-
Arrange with line managers for teams to work at home.
-
The BCM will make alternate arrangements for any staff unable to work from home.
-
-
Regular updates to our staff:
-
Within 2 hours of initial disaster.
-
Thereafter, each update should include an estimated time of when the next update will be sent.
-
-
Review likely length of location unavailability:
-
If projected to be less than 25 working days, initiate home working procedures.
-
If projected to be more than 25 working days, initiate allocate alternate office space, home working, or other alternatives.
-
-
Seek an alternate temporary location alongside remote working.
-
Regular updates to our customers:
-
Within 12 hours of initial disaster.
-
Thereafter, each update should include an estimated time of when the next update will be sent.
-
There won’t be a direct impact on service to customers. Therefore, updates should be weekly at most, sent via the usual Matrix Booking Customer Communications process.
-
-
Return to building:
-
Decide that office can be safely reopened.
-
Perform assessment of facilities.
-
Notify staff via the Matrix Booking all staff email of planned return.
-
-
Close recovery plan by ensuring the last update to staff and customers notes that the recovery is complete.
Recovery of Matrix Booking SaaS
The disaster recovery process will be activated under the following circumstances:
-
Any problem that would cause the above condition to be present or there’s certain indication that this condition is about to occur.
-
The BCM or Matrix Booking Lead deems a disaster has taken place.
-
The Matrix Booking Service is down concurrently for 5 or more hours.
Note: full loss of service will be treated as a priority 1 incident and responded to as such. If recovery takes less than 5 hours, the recovery processes won’t be invoked.
As Matrix Booking is hosted on AWS, they have continuity arrangements documented here: https://aws.amazon.com/compliance/data-center/controls/#Business_Continuity_.26_Disaster_Recovery
Initial communication and response
-
Maintain communication with AWS:
-
Raise high priority call with AWS at: https://console.aws.amazon.com/support/
-
Review call updates at: https://console.aws.amazon.com/support/
-
Follow up with any information requested from AWS.
-
Continue communication with AWS regarding responses.
-
-
Maintain communication with customers:
-
When the issue is first identified and hourly thereafter.
-
When new information received from AWS.
-
-
Respond to service restoration from AWS:
-
Assess impact on Matrix Booking’s software and data.
-
If the system is operational:
-
Inform customers.
-
Move to return to incident closure procedures.
-
-
If the system isn’t operational and further actions are required to restore software or data, follow Matrix Booking Software and Data Recovery procedures.
-
Details analysis and recovery
-
Perform detailed analysis of issue:
-
Determine likely causes of issue (for example, software, data, and so on).
-
Move to suitable recovery procedure (restart services, regress to earlier version, restore data).
-
-
Restart services if analysis determines this is appropriate course of action:
-
Restart back-end and web app pods.
-
Determine if issue is resolved.
-
If the system is operational:
-
Inform customers.
-
Move to return to incident closure procedures.
-
-
If the system isn’t operational, return to detailed analysis stage (1).
-
-
Regress to earlier version, if analysis determines this is appropriate course of action:
-
Determine the version to regress to.
-
Deploy the new version.
-
Determine if issue is resolved.
-
If the system is operational:
-
Inform customers.
-
Move to return to incident closure procedures.
-
-
If the system isn’t operational, return to detailed analysis stage (1).
-
-
Restore data, if analysis determines this is appropriate course of action:
-
Determine the latest data backup to restore to.
-
Inform customers of time period of data lost.
-
Restore AWS backup.
-
Determine if issue is resolved.
-
If the system is operational:
-
Inform customers.
-
Move to return to incident closure procedures.
-
-
If the system isn’t operational, return to detailed analysis stage (1).
-
-
Incident closure:
-
Agree with customers that incident is closed.
-
Contact customers and confirm the service is restored.
-
Declare incident closed.
-
Stand down Recovery team.
-
Schedule lessons learned session.
-
Initiate writing the Major Incident report.
-
Information security
Data Centre and physical security
Matrix Booking is hosted using AWS and to the extent that the Data Centre is controlled by AWS. Full details on controls in place can be found at: https://aws.amazon.com/compliance/data-center/controls/
AWS employee data centre access
AWS provides physical data centre access to only approved employees. All employees who need data centre access must first apply for access and provide a valid business justification. These requests are granted based on the principle of least privilege, where requests must specify to which layer of the data centre the individual needs access to and are time-bound. Requests are reviewed and approved by authorised personnel, and access is revoked after the requested time expires. Once granted admittance, individuals are restricted to areas specified in their permissions.
Third-party data centre access
Third-party access is requested by approved AWS employees who must apply for third-party access and provide a valid business justification. These requests are granted based on the principle of least privilege, where requests must specify to which layer of the data centre the individual needs access to and are time-bound. These requests are approved by authorised personnel, and access is revoked after request time expires. Once granted admittance, individuals are restricted to areas specified in their permissions. Anyone granted visitor badge access must present identification when arriving on site, are signed in, and escorted by authorised staff.
Data centre access review
Access to data centres is regularly reviewed. Access is automatically revoked when an employee’s record is terminated in Amazon’s HR system. Additionally, when an employee or contractor’s access expires in accordance with the approved request duration, their access is revoked, even if they continue to be an Amazon employee.
Data centre access logs
Physical access to AWS data centres is logged, monitored, and retained. AWS correlates information gained from logical and physical monitoring systems to enhance security on an as-needed basis.
Data centre access monitoring
We monitor our data centres using our global Security Operations Centres, which are responsible for monitoring, triaging, and executing security programs. They provide global support 24-7, every day of the year, by managing and monitoring data centre access activities, equipping local teams and other support teams to respond to security incidents by triaging, consulting, analysing, and dispatching responses.
CCTV
Physical access points to server rooms are recorded by Closed Circuit Television (CCTV) cameras. Images are retained according to legal and compliance requirements.
Data centre entry points
Physical access is controlled at building ingress points by professional security staff utilising surveillance, detection systems, and other electronic means. Authorised staff utilise multiple factor authentication mechanisms to access data centres. Entrances to server rooms are secured with devices that sound alarms to initiate an incident response if the door is forced or held open.
Intrusion detection
Electronic intrusion detection systems are installed within the data layer to monitor, detect, and automatically alert appropriate personnel of security incidents. Ingress and egress points to server rooms are secured with devices that require each individual to provide multiple factor authentication before granting entry or exit. These devices will sound alarms if the door is forced open without authentication or held open. Door alarming devices are also configured to detect instances where an individual exits or enters a data layer without providing multiple factor authentication. Alarms are immediately dispatched, 24-7 every day of the year, to AWS Security Operations Centres for immediate logging, analysis, and response.
Data archive and retention
Normally, booking data is held for the lifespan of the contract and potentially thereafter, based on agreement with the customer. However, the data retention period is at the customer’s discretion and will be kept for the lifespan of the contract unless it’s agreed to be incorporated into the Data Processing Agreement in place between the customer and Matrix Booking.
On termination of the subscription, the customer will be given full access to their static data for an agreed period as defined in the Data Processing Agreement, which will typically form part of the standard contract. Following this period, the data will be permanently deleted (or non-recoverable) from the Matrix Booking system.
Application security (penetration) testing
An annual CHECK level app security test (a penetration or “pen” test) is performed on Matrix Booking by a third-party CHECK-certified organisation (Cyberis).
Testing coverage includes OWASP Top 10 vulnerabilities and focusses heavily on the web app and API, which is a superset of all other Matrix Booking components.
Note: the most recent test was performed in September 2024.
Cyber security
Information classification
The organisation has an Information Classification scheme in place that allows staff to identify information that must be encrypted when being sent outside of the business. The details are as follows:
-
Client Sensitive:
-
Information received from a client that needs special handling, such as real data on their customers or employees.
-
Typically received for hosting or data migration.
-
-
Client Confidential:
-
includes information (for example, advice we give to a client or business partner, minutes of client meetings, technical or functional deliverables)
-
Tip: when receiving information from a customer, the customer’s classification scheme and means of transfer takes precedence.
-
Internal:
-
includes information that isn’t sensitive as to which staff can see it (for example, internal memos, ongoing project information or minutes of internal meetings)
-
-
Matrix Booking Internal Restricted:
-
includes business plans, company strategy, associated papers, employee details, internal policies, processes, procedures, legal advice, or the company’s financial data
-
-
Public:
-
includes information already available in the public domain (for example, marketing brochures, client or company details or other information)
-
Information risk management
Matrix Booking has an ISO 27001:2022 compliant Information Security Management System (ISMS) (for our current ISO 270001:2022 certificate, see Appendix).
Matrix Booking also maintains Cyber Essentials and Cyber Essentials Plus certification, externally audited annually (see Cyber Essentials certificates).
The Matrix Booking ISMS policy states that the ISMS will be externally audited to the standards of ISO 27001:2022 by a UKAS accredited auditor annually.
Matrix Booking Limited will measure the fulfilment of all the objectives of the ISMS. The ISMS Manager is responsible for setting the method for measuring the achievement of the objectives. The measurement will be performed at least once a year. The ISMS Manager will analyse and evaluate the measurement results and report them to the Chief Executive Officer (CEO) as input materials for the Management review. All ISMS policies must be reviewed once a year.
Secure configuration
Matrix Booking apply the National Cyber Security Centre (NCSC) secure configuration principles. They are as follows:
-
use supported software:
-
The underlying platform is supported by AWS.
-
-
develop and implement policies to update and patch systems:
-
The security patch management process mitigates threats and vulnerabilities.
-
The Security team rates security patches based on the Common Vulnerability Scoring System standard for operating systems, databases, and virtualisation in cloud services.
-
-
create and maintain hardware and software inventories:
-
All software had hardware components are stored in an IT asset register.
-
-
conduct regular vulnerability scans:
-
Penetration tests specific to Matrix Booking are performed annually.
-
-
establish configuration control and management:
-
Matrix Booking configuration manage the system. Known labelled deployments are made from a version control system.
-
All Matrix Booking systems are built to standardised build sheets. This is further reinforced by automated builds where possible.
-
-
disable unnecessary peripheral devices and removable media access:
-
All systems in the stack are hardened meaning that all non-essential services are deactivated in the system.
-
User accounts that aren’t required are deleted.
-
-
implement whitelisting and execution control:
-
The only software that can be executed within the Matrix Booking container is the Matrix Booking software.
-
-
limit user ability to change configuration and limit privileged user functionality:
-
The principle of least privilege is applied and only authorised administrators can deploy new code to the Matrix Booking system.
-
Network security
The Matrix Booking platform runs on cloud infrastructure. This is set up in a fenced network, separated from the other networks. The internal traffic is controlled by firewalls. The network is zoned into tiers with ACLs between. All external transmission is secured using strong TLS.
System access control
For technical administrators, Matrix Booking:
-
apply principle of least privilege to system access, so Matrix Booking team members get the least amount of access they need to do their jobs
-
have separately controlled access for development, testing, and production
-
access is regularly reviewed, and access right removal is part of our joiners, movers, and leavers processes
-
all Matrix Booking staff and contractors receive security training upon induction, with mandatory annual refresher training
Mobile security
Our apps are set up to use https and Transport Layer Security (TLS) for network traffic. This means that all information is communicated securely to the back-end servers.
User education and awareness
All Matrix Booking staff and contractors receive security training on induction, with mandatory annual refresher training. Training is identical for permanent and temporary staff.
Security incident management
In accordance with ISO / IEC 27000:2009, an information security incident is a "single or a series of unwanted or unexpected information security events that have a significant probability of compromising business operations and threatening information security."
There are several ways security incidents may arise:
-
incidents or breaches reported by or directly impacting a specific customer to which we provide a managed service
-
internal incidents related to IT
-
internal incidents related to staff action
The Matrix Booking ISMS includes a Cyber Incident Response procedure that include the processes for notification of impacted parties, remediation, and lessons learnt. Incidents are tracked via our 24-7 service desk. Matrix Booking staff and customers can raise security incidents with the Matrix Booking IT help desk.
Malware prevention
Matrix Booking recognises that viruses are a major threat to the organisation and laptops are particularly vulnerable if their antivirus software isn’t kept up-to-date. Matrix Booking-issued laptops are managed centrally via Sophos antivirus software.
Matrix Booking’s IT team are responsible for the management of the central antivirus system and will ensure your laptop is updated. If you have any concerns that this isn’t happening, contact the Matrix Booking IT help desk.
Virus scans on all attachments and files happen automatically, but the ISMS Manager trains staff on how to initiate manual scans if there are files that they need to ensure are safe.
Removable media
Removable media includes, but isn’t limited to:
-
USB memory sticks
-
portable hard drives
-
CD-ROMs
Note: the use of these is avoided where possible.
Electronic data transfers using OneDrive or similar mechanisms preferred.
For all customer-sensitive data, we ensure the transfer method, including any intermediate storage, is agreed in advance with the customer if it’s outside of our standard security methods.
Cryptograph controls
The following cryptograph controls are deployed across the Matrix Booking operations:
-
data in transit
-
Any data (other than Matrix Booking public) should be encrypted in transit (unless between 2 hosts in a locked down secure subnet).
-
-
permitted standards are:
-
TLS (minimum version 1.2)
-
SSH 2
-
-
data at rest:
-
Any data (other than Matrix Booking Public) is encrypted using industry standard 256-bit Advanced Encryption Standard (AES-256).
-
-
encryption keys:
-
Encryption keys should be kept in Matrix Booking’s secure backed up repositories with authorisation to access keys granted, according to the principle of least privilege.
-
Keys must be generated in a secure manner with strong pass phrases, and where possible, dual control should be followed, with 1 person generating the key and another loading the key.
-
hen keys need to be distributed:
-
The distribution list must be limited to those who need it
-
The channel must be secure, with encryption and required authentication.
-
Keys and authentication to them (for example, pass phrases must be sent separately), and where possible, by separate channels.
-
-
Keys should be rotated at least annually.
-
If a key is suspected as being compromised, it must be replaced immediately.
-
Privacy and data protection
Compliance with privacy and data protection legislation
Matrix Booking has an Information Security Compliance programme that considers relevant legislation, including the requirements set out in the:
-
Data Protection Act 2018 of the UK Parliament
-
General Data Protection Regulation (GDPR) 2016 / 679 of the European Union (EU) and European Parliament
Matrix Booking maintains policies for data privacy and protection including:
-
policies for data protection and retention:
-
Matrix Booking maintains a set of policies for the storage, protection and retention of data.
-
Along with procedures to address and review enquiries by individuals related to the data we hold on them, these policies, and the monitoring thereof, are overseen by Matrix Booking’s board of directors.
-
-
procedures for dealing with data breaches:
-
Matrix Booking has procedures to respond to data breaches, which include notifying the appropriate authorities and individuals concerned.
-
-
Data Protection Officer (DPO):
-
Matrix Booking has appointed a DPO who is responsible for ensuring the overall GDPR compliance for all Matrix Booking’s personal data processing activities. The DPO reports directly to Matrix Booking’s CEO and can be contact by customers using the address: dpo@matrixbooking.com
-
-
staff awareness:
-
All staff and associates receive mandatory data privacy and protection awareness training upon joining and through annual refresher courses.
-
-
data integrity and security:
-
Matrix Booking has a firm commitment to data security, integrity, and protection by being certified to the ISO 27001:2022 ISMS standard, to ensure we have appropriate organisational and technical data protection controls in place.
-
Note: for the current Matrix Booking ISO 27001:2022 certificate, see Appendix.
-
suppliers:
-
We take appropriate steps to assess our suppliers’ potential risk and ensure we have GDPR clauses in all our supplier agreements when required.
-
Matrix Booking will, through appropriate management, strict application of criteria and controls:
-
fully observe the conditions regarding the fair collection and use of information
-
meet its legal obligations to specify the purposes for which information is used
-
collect and process appropriate information, and only to the extent that it’s needed to fulfil operational needs or to comply with any legal requirements
-
ensure the quality of information used
-
apply strict checks to determine the length of time information is held
-
ensure that rights of people about whom information is held, can be fully exercised
-
take appropriate technical and organisational security measures to safeguard personal, and deal with Subject Access Requests
-
contact the Data Controller to correct or erase any information on an individual that’s inaccurate or misleading
-
not use information for a purpose which is incompatible with the original purpose for which permission was given by the data subject
-
obtain clear, express permission for handling and using ‘sensitive’ personal data, such as race, ethnicity, political opinions, religious beliefs, trade union membership, state of health both physical and mental, sexual life, criminal convictions and sentences, and allegations of criminal behaviour (Matrix Booking doesn’t capture or hold any sensitive data)
-
treat people justly and fairly whatever their age, religion, disability, gender, sexual orientation or ethnicity when dealing with requests for information
-
set out clear procedures for responding to requests for information
-
allocate such resources as may be required to ensure the effective operation of the Policy
Keeping personal data and unauthorised access or disclosure
Matrix Booking data is stored in the EU only. Data is regularly backed up, with transmission to a second data centre for further resilience. The Matrix Booking Compliance team reviews our platform for compliance with relevant privacy and data protection legislation. All data transmission in our “out-of-the-box” solution is encrypted using TLS, with system logs shipped to an immutable third-party store for audit. Matrix Booking is a global platform and as a data processor (and in certain circumstances a sub-processor) we ensure the privacy of data in the Matrix Booking system and compliance with GDPR by carrying out the following:
-
identifying personal data:
-
The personal data that Matrix Booking captures is the minimum required to provide the service, and all the modules of the system have been reviewed to ensure this principle is adhered to.
-
-
providing visibility and transparency:
-
One of the key elements of GDPR is access to data for our customers as Matrix Booking has always been open and transparent with the data, and the administrators of the system have always had the ability to view all information when required.
-
Matrix Booking is also in the process of identifying key data protection staff within each of our client organisations as well as growing our own.
-
-
enhancing data integrity and security:
-
With the ever-increasing importance on individual’s data privacy and security, Matrix Booking continually reviews and tightens its security controls and processes to provide complete confidence to our customers, which ranges from continual improvement via ISO frameworks through to technical and architectural enhancements in cloud security provision.
-
-
portability and transferability of data:
-
GDPR allows any user of the system to request their data, so Matrix Booking has always had the ability to extract all information as and when required via an organisations own administrators, so giving EU residents (although we apply this to all users of the Matrix Booking products and modules) the right to either:
-
receive all the data provided and processed by the controller
-
transfer it to another controller or processor depending on technical feasibility
-
-
Mobile data protection
No credentials are hardcoded into the app meaning the authentication process can’t be bypassed. To log in, you must use your login credentials (email address or username and password) or via our SSO integration. For more information, see SSO.
The Matrix Booking mobile app stores each user’s email address and Matrix Booking settings data required for the app to function correctly on that user’s mobile device. A temporary authentication token is also persisted to facilitate quick access to the application.
We use code obfuscation to prevent our apps from being infiltrated and compromised.
Supply chain accreditation
Our ISO 27001 certified ISMS includes processes to ensure that our sub-contractors provide appropriate levels of security, privacy, and resilience. The key to the Matrix Booking service are our hosting partners Amazon Web Services (AWS), who provide the cloud platform on which the service runs and hosts supplementary location data. The Data Breach Response team will convene for each reported (and alleged) personal data breach and will be headed by the Data Breach Response Team Leader.
Screening employees and temporary workers
Matrix Booking’s Referencing and Security Clearance Policy ensures that all permanent and temporary employees are appropriately screened in accordance with BS7858:2019. This includes:
-
all staff:
-
identity check, including name and date of birth (DOB)
-
sight of original passport and a copy is for file
-
home address provided and stored on file
-
National Insurance number and stored on file
-
check of visa status and copy taken for file
-
with 2 references and stored on file
-
-
additional checks (where necessary):
-
Disclosure and Barring Service (DBS)
-
Baseline Personnel Security Standard (BPSS)
-
credit check
-
directorship and media check
-
adverse media checks
-
Supporting subject access requests
Any subject access request received by Matrix Booking relating to a specific customers account or visitor to a customer organisation will be emailed directly to your organisations Data Protection Officer (if we have been provided with this), if we haven’t been given a “DPO” contact, we’ll raise a support ticket in our Support Portal for this request and assign it to your own organisations Matrix Booking administrators for them to fulfil. As Data Processors, we aren’t authorised to respond to a Subject Access Request on your behalf, so we’ll acknowledge the request and advise that we’re passing this on to the Data Controller and pass this directly on to you.
Privacy and data protection assurance activities
The Matrix Booking system has the following audits in place:
-
System audit logs are shipped to a separate system for review.
-
Annual ISMS audits by an external UKAS accredited auditor.
-
The ISMS includes policies to ensure adherence to regulatory and contractual requirements.
-
Appendix
Matrix Booking’s ISO 27001 certificate

Matrix Booking’s Cyber Essentials certificate

Matrix Booking’s Cyber Essentials Plus certificate

Amazon Web Service ISO 27001 certificate
Full certification detail available at: https://d1.awsstatic.com/certifications/iso_27001_global_certification.pdf

Sub-processor list
Matrix Booking acts as a data processor (and in certain circumstances such as hub and tenant environments, we act as a sub-processor) and can provide a Data Processing Agreement (DPA) on request. Although, this would normally form part of your customer contract / agreement.
For more information, see list of sub-processors.