This page covers the single sign-on (SSO) and directory integrations between your organisation’s directory and Matrix Booking.
Contents
Introduction
Bypass the web app’s login screen
Let people log into Matrix Booking using the same details they already use for your other IT systems. Matrix Booking integrates with your corporate single sign-on system either via OAuth 2.0 or SAML 2.0. This also enables you to implement multi-factor authentication when people log into Matrix Booking using your corporate identity provider.
This can be achieved by providing users with an SSO redirect link. To get the URL for this link, raise a support ticket. If your organisation has multiple SSO integrations in place, you’ll be provided with a different URL per SSO integration.
The SSO redirect link works by forwarding the user to the corresponding SAML identity provider (IdP) and the user may be required by the IdP or authorisation server to authenticate first – if the user is already authenticated, they will be taken directly into the Matrix Booking web app without the need to authenticate again.
Notes:
-
It’s only possible to bypass the Matrix Booking login screen in the web app.
-
Our suite of apps, such as Signage and Floor plan, don’t support SSO – organisations with SSO setups will either need to allow booking, starting meetings and ending meetings, to be performed anonymously, or for these functions to be disabled on the device.
Directory synchronisation
Keep your Matrix Booking user list up to date when people join, change roles, or leave by integrating with your existing Entra ID system or using System for Cross-domain Identity Management (SCIM). This has the added benefit of letting you link resource permissions to the security groups people are in in the Entra ID system. This can make it simple to ensure only employees in a particular region can book resources in a certain building.
Matrix Booking also lets you set up and manage advanced, domain, and user groups within the software.
SSO integration requirements
Choose the right SAML NameID
Matrix Booking makes sure that a user’s account and their booking history is maintained. For example, if a user’s email address has been changed, our system uses the SAML NameID to identify the user’s account.
However, this only works if the SAML NameID remains the same. If you’re using Microsoft AD FS or Entra ID, we recommend that the SAML NameID contains either:
-
user principal name (UPN) (default)
-
object ID
Matrix Booking uses POST SAML bindings. The assertions contained in the SAML response must be signed and include:
-
NameID – a unique identifier for the user and one that ideally won’t change.
-
email
-
firstName
-
lastName
Notes:
-
If your organisation changes usernames when they have had a change of name, it’s recommended that you use the object ID. This is because if you change the name in Microsoft Azure, Matrix Booking will assign the same person a new user account because our system won’t recognise the name change.
If you use the object ID, it remains the same regardless of a name change. Therefore, Matrix Booking can maintain the user’s account and their booking history. -
We expect the object ID to be passed as a base-64 encoded value.
Advanced setup: multiple Matrix Booking organisations from a single IdP
If multiple organisations using Matrix Booking need to be serviced from a single IdP, you’ll need to make a unique Entity ID to each application. The default Entity ID is “app” in “app.matrixbooking.com” within the .xml metadata file.
If more applications are needed, give a different Entity ID for each 1 in the following format: [unique Entity ID].matrixbooking.com. For example, “other_org.matrixbooking.com”.
Entra ID integration requirements
Matrix Booking must be registered as an Enterprise Application or an App Registration in the Microsoft Azure Portal.
You need our SSO integration to use our Entra ID directory integration. This integration uses the Microsoft Graph API (application programming interface) and if you make any changes to your organisation’s internal directory in Entra ID, it will be reflected in Matrix Booking. They can be easily searched for when assigning bookings or adding attendees.
The directory sync will automatically create, deactivate, or reactivate leavers and joiners in Matrix Booking. This is useful for preventing access to Matrix Booking when a user leaves your organisation who is already logged into Matrix Booking.
We support:
-
Entra ID sync via the Graph API.
-
SCIM.
Note: we don’t support any other directory integrations.
Security
Matrix Booking provides your organisation with the flexibility to choose how people register as users and subsequently log in. You may wish:
-
To allow users to self-register using an email address and password that meets your organisation’s email and password rules.
-
To send explicit invites to a person’s email address, who can then self-register using a password that meets your organisation’s password rules.
-
For users to be automatically registered using details passed to Matrix Booking after a successful SSO flow.
You can choose any of the above or have a mixture of them. We can support SSO where your identity provider, such as Microsoft Azure Active Directory Federation Services (ADFS) or Entra ID, supports SAML 2.0. Multiple identity providers can also be supported.
Account security
Account holders and users want a seamless user experience without comprising their security. An example of making the user experience better was the introduction of single sign-on (SSO), where a user only needed to log in once rather than having to repeatedly do this.
You want the assurance that your users’ accounts and processes are safe and used correctly. We can offer that security through different approaches, some of which are blended. The processes for setting up your desired security approach will require the involvement of your organisation’s IT teams and our Support Team.
Security assertion markup language (SAML) 2.0
When implementing SAML-based SSO, Matrix Booking acts as the service provider (SP) that participates in authentication flow with your organisation’s identity provider (IdP). Matrix Booking supports both SP-initiated and IdP-initiated SSO flows.
The SP-initiated flow is comprised of the 5 steps.
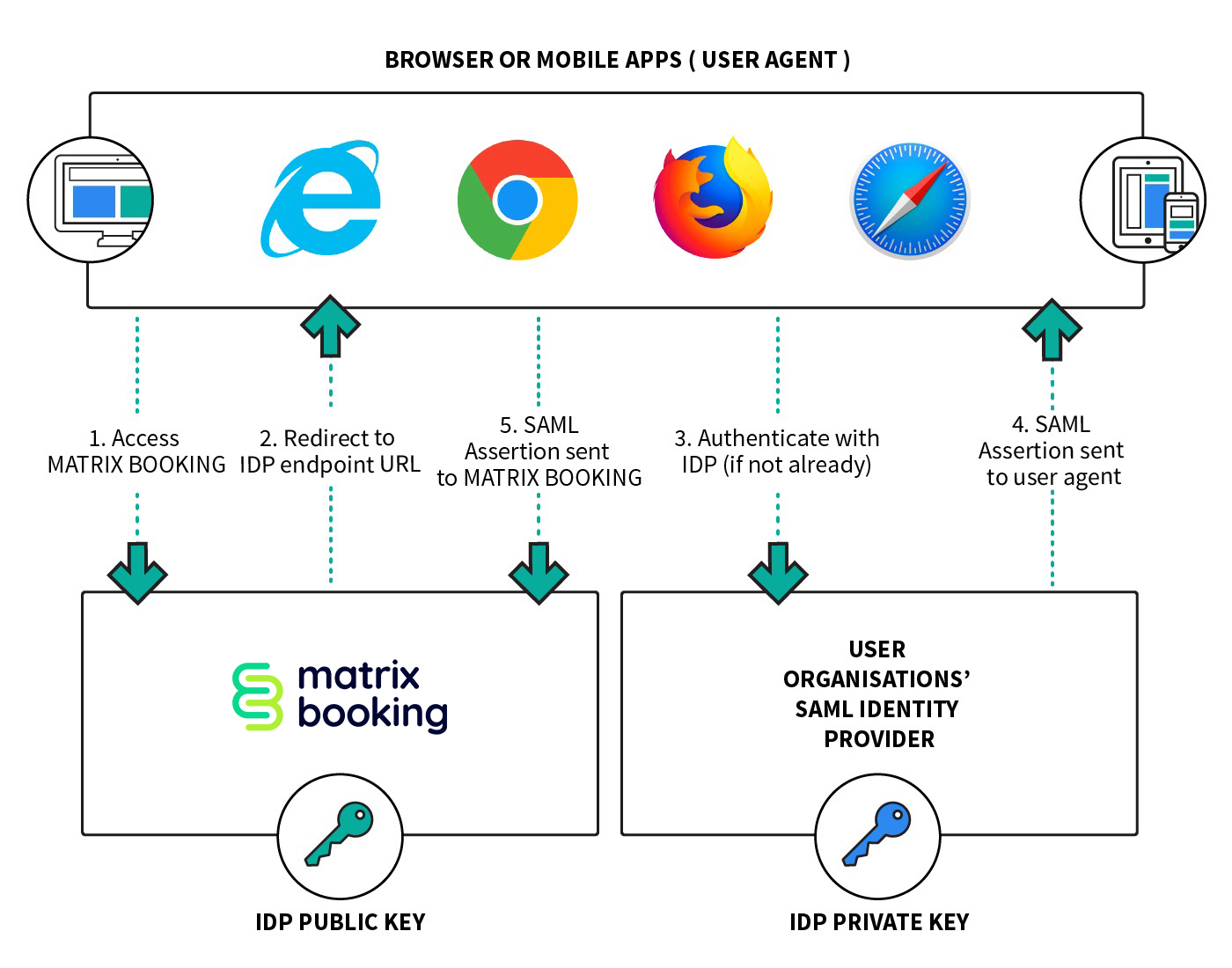
The user enters their email address on the Matrix Booking login screen, either through the web or mobile apps or the add-in. Matrix automatically checks the email address to see if a SSO setup is in place and shows a button, such as Login with SSO.
Warning: the text for this button may differ.
The Matrix password field is usually hidden. However, you can change this as a part of your configuration.
When the SSO login button is selected, Matrix Booking re-directs the user to the IdP login page. If supported by the IdP, Matrix Booking can also send through the entered email address so that the user doesn’t need to enter it again.
The user authenticates with the IdP using their SSO password. It’s possible that the IdP doesn’t require authentication if the user is already authenticated. Once the user is authenticated, the IdP forms a SAML response, which is returned to the Matrix client (for example, the web or mobile app).
The Matrix client passes the SAML response to Matrix Booking, where it’s verified against previously exchanged certificate data. If the user account is valid, it will allow the user to continue into the Matrix Booking app fully authenticated.
The IdP-initiated flow permits a user to select Matrix Booking from within their environment, such as Google Workspace or Okta. The appropriate SAML response will be sent to Matrix Booking as per step 5 of the SP-initiated SSO flow.